What is Cold Wallet?
In today’s rapidly evolving technological landscape, cyberattacks targeting investors’ crypto assets are becoming increasingly sophisticated. Threats such as malware, phishing links, and social engineering techniques are becoming increasingly common among malicious actors.
As such, it’s crucial for investors to secure their crypto assets properly, starting with choosing the right type of wallet and implementing effective preventive measures. One of the safest methods available is the cold wallet — a crypto wallet that is not connected to the internet.
Cold wallets have been the industry standard for institutional and individual investors who prioritize maximum security when storing their crypto assets for a long time.
This article will explore cold wallet in depth, covering their definition, how they work, their advantages and disadvantages, and other key information you need to know. By the end, you’ll understand why choosing a secure storage method is crucial for protecting your crypto assets.
Article Summary
- 📟 Cold Wallet: a crypto wallet that stores your private key offline, disconnected from the internet, making it highly resistant to cyber threats like phishing and malware.
- ❄️ Cold wallets are ideal for long-term storage, offering maximum security but requiring users to keep their seed phrase safe at all times.
- 📠 Users can still fall victim to malicious transaction approvals, even with a secure device.
- 🌟 Combining a cold wallet for long-term holdings with a hot wallet for daily use is the most effective crypto storage strategy.
What Is a Cold Wallet?
A cold wallet is a type of crypto wallet that stores the private key offline, without a direct internet connection. Typically, these are physical devices (hardware wallets) that resemble USB drives and are only connected to a computer or other device when the user wants to initiate a transaction.
Technically, the crypto assets are not stored physically on the wallet. Instead, they remain on the blockchain network. However, cold wallet enhance security by keeping the private key — which is used to authorize transactions — offline, making it less vulnerable to internet-based attacks.
How Cold Wallet Work
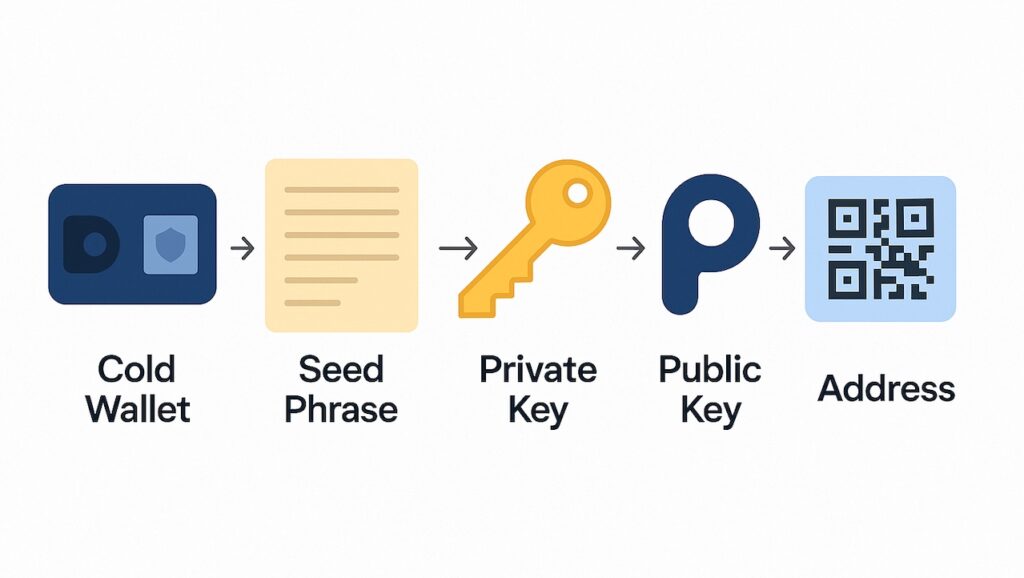
When first initialized, a cold wallet generates a seed phrase, consisting of 12 or 24 random words that appear once and must be carefully recorded and securely stored. This seed phrase is the only way to recover access to the wallet if the device is lost or damaged.
Cold wallets generally do not display the private key directly. Instead, they derive the private key internally from the seed phrase. From the private key, a public key is generated, and from the public key, the user’s wallet address is formed to receive crypto assets.
Because of this structure, safeguarding the seed phrase and private key is critically important. If this information falls into the wrong hands, all the crypto assets stored in the wallet could be accessed and stolen without a trace.
Devices such as the Ledger Nano X, for example, will prompt users to create a new wallet (by generating a new seed phrase) or restore an existing one using a previously saved seed phrase. Once set up, the device can be paired with official applications like Ledger Live, which allow users to view balances, manage assets, and initiate transactions. However, all cryptographic processes, including key storage and transaction signing, are handled securely within the cold wallet and never exposed to the internet.
How Transactions Work with a Cold Wallet
Here is a typical process for making a transaction with a cold wallet:
- The user initiates the transaction using an official app (e.g., Ledger Live) by selecting the asset, amount, and recipient address.
- The app sends the transaction details to the cold wallet for signing.
- The cold wallet prompts the user for confirmation, then signs the transaction offline.
- Once signed, the transaction is sent back to the app to be broadcast to the blockchain.
Because the private key never leaves the device, this process offers maximum security even when using internet-connected computers or smartphones.
Why Use a Cold Wallet?
Cold wallets are ideal for investors seeking highly secure, long-term storage of crypto assets, whether the holdings are small or substantial. However, using a cold wallet comes with added responsibility, particularly in safeguarding the seed phrase and understanding how the device functions. Without proper knowledge, users risk losing access to their own assets.
Therefore, cold wallets are strongly recommended for those who are ready to manage their crypto assets independently.
Advantages and Disadvantages of Cold Wallets
While cold wallets are widely regarded as the most secure storage option due to their offline nature, it’s essential to understand both their strengths and limitations before deciding to use one.
Advantages of Cold Wallets
- Extremely Resistant to Hacking
Cold wallets are used solely to sign transactions offline, without being connected to the internet. The private key remains stored within the device and never exposed online, significantly reducing the risk of cyber threats such as phishing, malware, or remote hacking. This makes cold wallets the top choice for long-term crypto storage. - Full Ownership and Control
Cold wallet users have complete control over their wallets and private keys. The private key generated during wallet setup is stored solely on the device. This means only the device owner can access, transfer, or manage the assets, provided they have the seed phrase or a secure backup. - No Reliance on Third Parties
Cold wallets do not depend on external services or online platforms to access assets. As long as the seed phrase is kept safe, users can recover their wallets on a new device at any time. This adds resilience against system failures or attacks on service providers. - Recoverable Anytime
Although users are fully responsible for securing their cold wallets, accidents like losing the device can happen. Fortunately, as long as the seed phrase is securely stored, the wallet can be recovered on a new, compatible device. Once recovered, users can sign new transactions directly from the new device without needing the old one. As an extra security measure, it is advisable to transfer assets to a new address generated by the recovered device to mitigate any risk of seed phrase exposure.
Disadvantages of Cold Wallets
- Risk of Asset Loss
Unlike crypto exchanges (such as Pintu) that offer account recovery features like “forgot password,” cold wallets do not have such mechanisms. If a user loses the device and has not safely recorded their seed phrase, wallet access cannot be restored. As a result, all crypto assets stored on the wallet may be lost permanently. This underscores the critical importance of securely recording and storing both the device and the seed phrase. - Less Practical for Daily Use
Because cold wallets are not always connected to the internet, they are not ideal for users who frequently transact, such as daily traders or those active in the DeFi ecosystem. Each transaction requires manually connecting the device and authorizing it through the companion app. - Vulnerable to Malicious Transaction Approvals
Although cold wallets are known to be very secure against hacking because they store private keys offline, users can still become a target of hacking if they are not careful when approving transactions. Scammers may send seemingly legitimate transaction requests, and if approved without proper verification, they can gain access to the user’s funds.
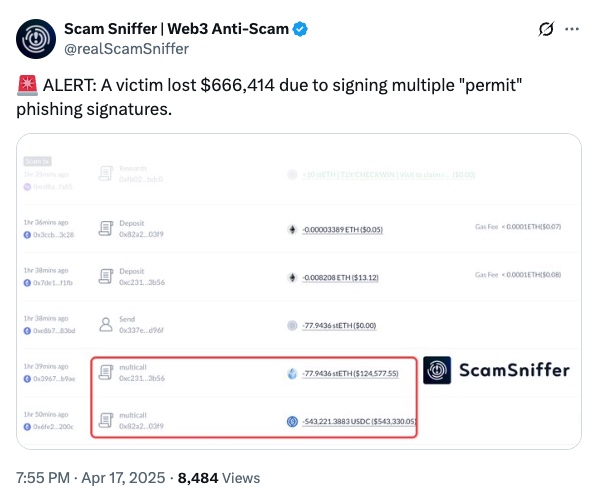
For example, a user reportedly lost over $666,414 after unknowingly approving a phishing transaction that gave a scammer full access to the wallet.
Comparison: Cold Wallet vs Hot Wallet
| Aspect | Cold Wallet | Hot Wallet |
| Connectivity | Offline; not connected to the internet | Always connected to the internet |
| Security | Very secure; private key never exposed online | More vulnerable to cyberattacks (phishing, malware, etc.) |
| Accessibility | Less practical; requires manual steps to connect and transact | Easily accessible via internet-connected apps or browsers |
| Cost | Requires purchase of hardware (approx. IDR 1M – 5M) | Typically free |
| Loss Risk | Risk of losing device or seed phrase with no recovery option | Risk of hacking or phishing attacks via online vulnerabilities |
| Examples | Ledger Nano X, Trezor Model T, SafePal | MetaMask, Trust Wallet, Phantom |
As shown in the table above, cold wallets offer superior security, while hot wallets excel in accessibility and convenience.
Disclaimer: All articles from Pintu Academy are intended for educational purposes only and do not constitute financial advice.
Conclusion
Cold wallets are one of the most secure methods for storing crypto assets because they keep private keys offline, away from internet-based threats like phishing or malware. These wallets are especially suitable for investors looking for long-term storage and who prioritize security.
However, using a cold wallet requires a strong sense of personal responsibility. Users must understand how the wallet works and ensure the seed phrase is safely stored. Losing access to the seed phrase can result in permanent loss of assets. Additionally, while cold wallets are offline, they can still be compromised if users unknowingly approve malicious transactions.
Meanwhile, hot wallets remain a popular option due to their ease of access and suitability for daily activities like trading or interacting with DeFi apps. However, they carry higher risks if not used carefully.
To strike a balance between security and convenience, it’s advisable to use both: cold wallets for long-term storage of the majority of assets and hot wallets for day-to-day transactions involving smaller amounts.
With the right understanding and responsible usage, you can protect your crypto assets while staying flexible in how you use them.
References
- Ledger Academy, “What Is a Cold Wallet?,” ledger.com, accessed April 17, 2025.
- Investopedia Team, “Cold Storage: What It Is, How It Works, Theft Protection,” Investopedia, accessed April 17, 2025.
- Dave Birnbaum, “What Is a Cold Wallet?,” Forbes, accessed April 17, 2025.
- JSXPRO ID, Ledger Nano X – Complete Tutorial, Youtube, accessed 17 April 2025.
Share