What is a Wallet Drainer and How to Avoid It?

As a crypto investor or trader, it’s crucial to be aware of the threats that could endanger your assets. One impending threat in the crypto industry is the wallet drainer. In this article, we will explain what a wallet drainer is, its characteristics, and tips on how to avoid these scammers.
Article Summary
- 🚨 A wallet drainer, or crypto drainer, is a type of malware that targets crypto wallets by deceiving victims into approving transactions that can drain all their assets.
- 🧟♂️ Phishing and ice phishing are the two most common activities of wallet drainer culprits.
- 💰 Inferior Drainer managed to drain assets worth $29 million, followed by Venom Drainer stealing nearly $27.5 million in assets, and Pink Drainer taking more than $3 million in assets.
Definition of Wallet Drainer
A wallet drainer or crypto drainer is a type of malware that targets crypto asset wallets. This malware works by tricking victims into authorizing malicious transactions, allowing for the complete draining of assets in their wallets. Perpetrators of wallet drainers typically use them in phishing attacks, where victims are tricked into clicking malicious links or opening dangerous attached documents.
How Does Wallet Drainer Work?
The modus operandi of wallet drainer perpetrators is to exploit vulnerabilities in the way crypto wallets work. When transferring crypto assets from one wallet to another, a transaction signature using a private key is required. This private key acts like a password and allows authentication or authorization of transactions from the crypto wallet.
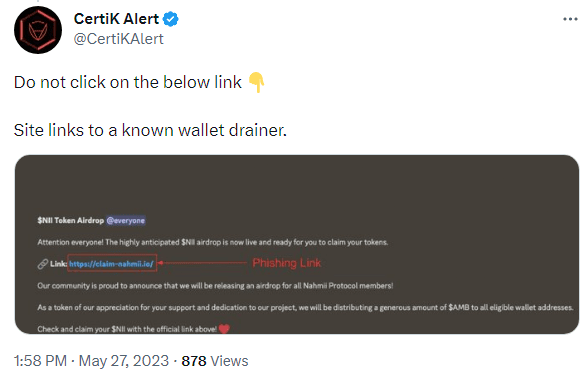
The most common example of wallet drainer activity is shown in the image above. In this scheme, the attacker provides a link that, when clicked, launches a transaction that requests a signature from the wallet owner. If the user isn’t careful, they may unknowingly click on this link, and as a result, the transaction requests access to all the assets in the wallet. Wallet drainer perpetrators target users who are less vigilant and do not thoroughly review each transaction they process.
Types of Wallet Drainer
The modus operandi of wallet drainer perpetrators revolves around tricking victims into signing malicious transactions that result in the loss of all of the victim’s assets. There are several methods used by these perpetrators, including:
Phishing
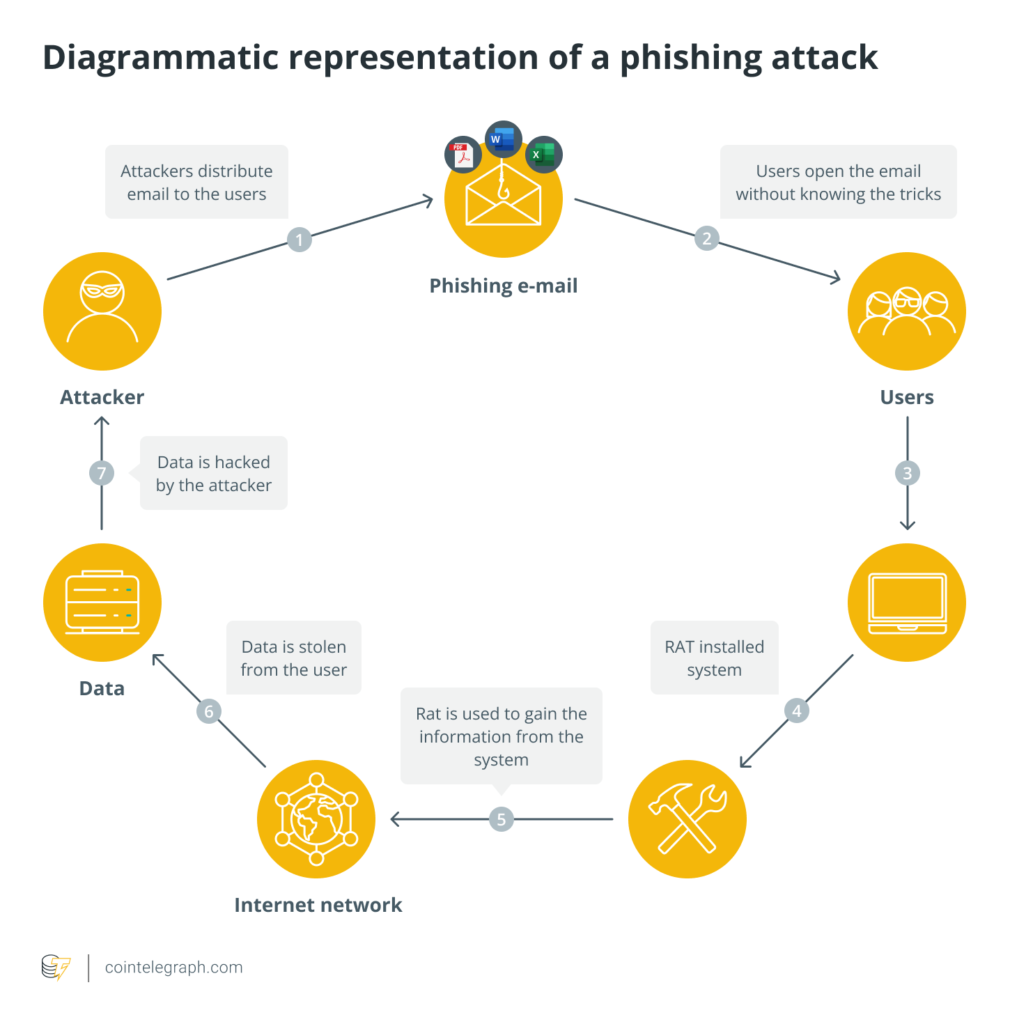
Phishing is a concept that’s been around since the Web2 era. In this method, attackers attempt to steal confidential user information by posing as legitimate entities and tricking users into revealing secret information such as passwords or parents’ names. Phishers typically pose as banking sites or customer service representatives. With the advent and rise of Web3, these attackers have adapted their techniques to target the confidential information that is a user’s crypto-wallet private key.
Ice Phishing
Ice phishing is a technique where users are tricked into signing a transaction that gives the attacker control over the user’s tokens without revealing the private key. This can happen with major token standards such as ERC-20, ERC-721, and ERC-1155. All three standards implement an authorization function that allows users to delegate authority to a third party, such as a decentralized exchange (DEX), to act on the user’s behalf for that specific token.
According to Forta, a blockchain security company, this technique accounted for 55.8% of all attacks on crypto wallets in 2023, specifically in May.
An example of ice phishing occurred on December 17, 2022. A hacker successfully stole 14 Bored Apes non-fungible tokens (NFTs) from the famous Bored Apes Yacht Club (BAYC) collection. An investor was tricked into signing a transaction request disguised as a movie contract, allowing the scammer to sell all of the user’s NFT Apes to the hacker at a bargain price.
The hacker’s process is illustrated in the image below.
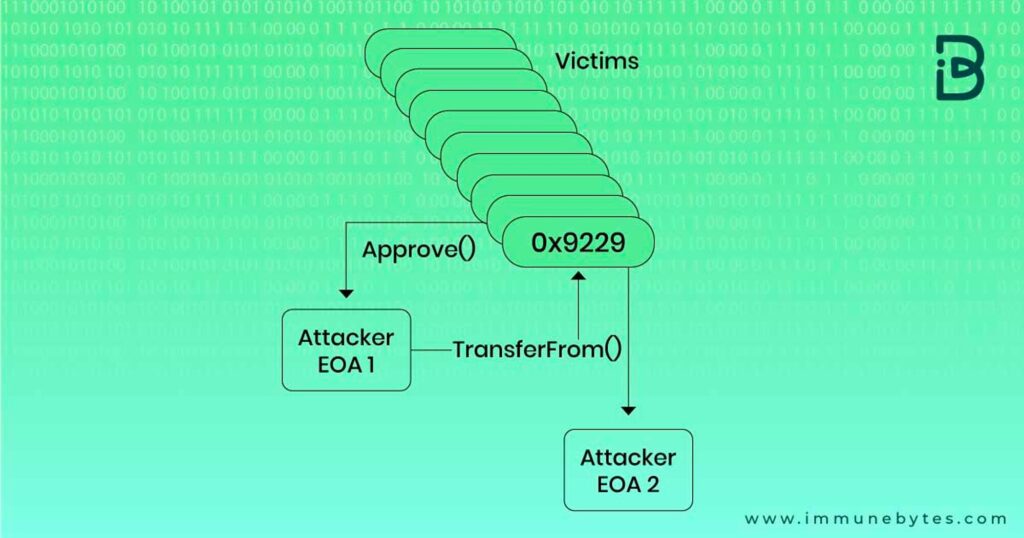
How to Avoid a Wallet Drainer
- Be cautious about clicking on links in emails or opening attachments from unknown senders. If you’re not sure about the legitimacy of an email, it’s best to ignore it. Also, refrain from signing any suspicious transactions.
- Read the transaction details carefully before granting permission and signing the transaction. Never click on links from unknown or suspicious sources.
- Crypto wallets are constantly evolving. Use crypto wallets that can alert you to potentially fraudulent and hacked transactions before you authorize them.
- Do Your Own Research (DYOR). Scammers often use high-pressure tactics to get you to invest without adequate research. When considering an investment, take the time to learn more about the project or token. Also, make sure the information comes from reputable sources.
- When minting NFTs, it’s best to use a newly created or empty wallet. Wallet drains can’t work if there is nothing to drain. Never use an active wallet to mint NFTs.
- Store your crypto assets in a hardware wallet. A hardware wallet is a physical device that stores your private key offline, making it much more secure than cold wallets stored on computers or phones.
Example of a Wallet Drainer
Venom Crypto Drainer
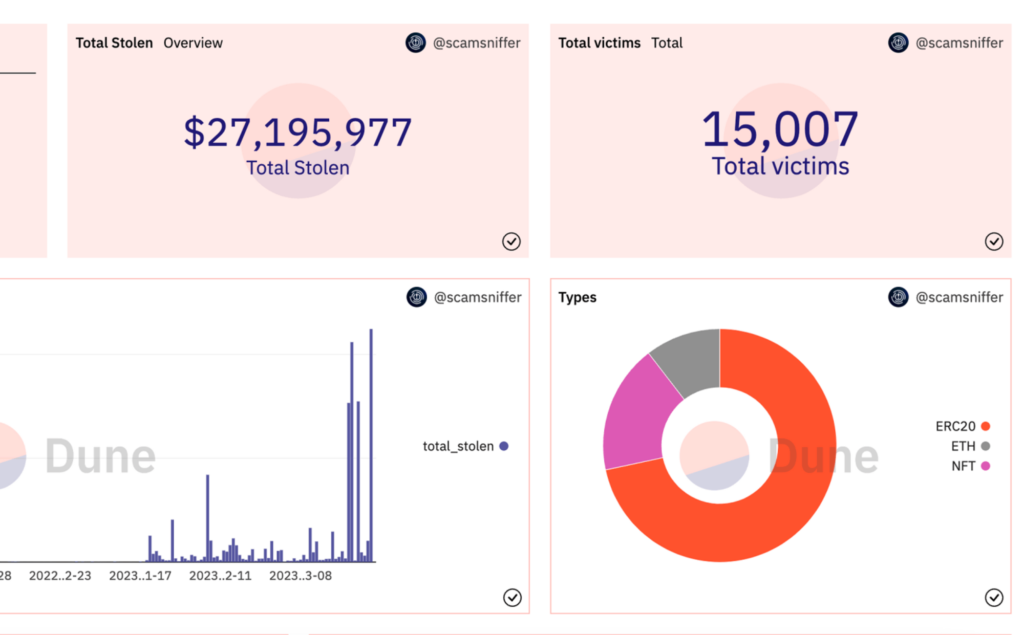
Venom Crypto Drainer is infamous in the world of wallet drainers. According to data from Dune Dashboard, supplemented by Web3’s Scam Sniffer anti-fraud platform, Venom Crypto Drainer has drained over 15,000 wallets, with a total of $27.5 million in assets stolen as of February 2023.
According to current data from looker.studio.google.com, there are approximately 546 phishing sites created by Venom Crypto Drainer, targeting more than 173 brands. Some of these targeted brands include Arbitrum, Circle, Blur, zkSync, Optimism, Shibarium, GPT, Trust Wallet, Metamask, Aptos, Adidas, Rocket Pool, Uniswap, and others.
The affected chains are ERC20 – 20,789,790, ETH – 3,122,586 and NFT – 5,332,332. In practice, Venom Crypto Drainer uses the “Permit and Approve” phishing method. For ERC20, the attacker tries to get the wallet owner to approve a transaction and then proceeds with the transfer using the ERC20 token.
Inferno Drainer
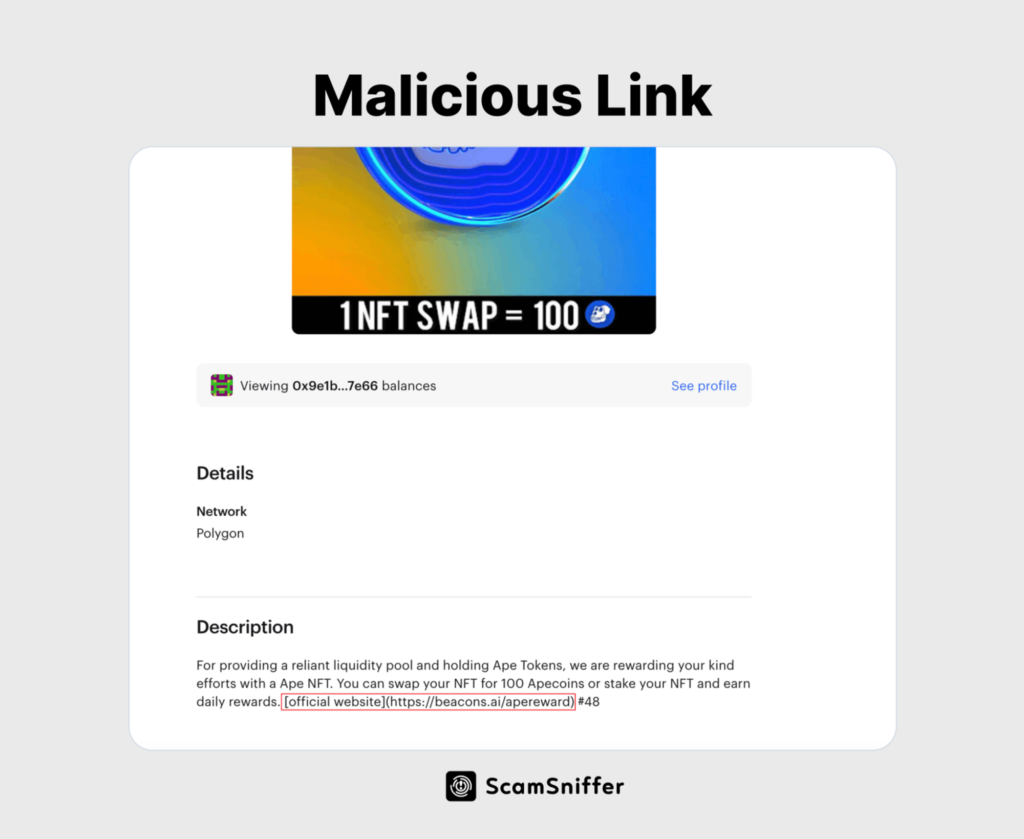
Inferno Drainer is another wallet drainer that has been used to steal more than $29 million from 70,000 victims. Inferno Drainer operates as a syndicate in multichain scams, claiming 20% of the stolen funds. Inferno has created over 600 phishing sites targeting over 220 brands, including Pepe, Collab.Land, Bob, Optimism, Sui, zkSync, PSYOP, and hundreds more.
Inferno Drainer works by using fake NFT airdrops, as seen in the image below:
Pink Drainer
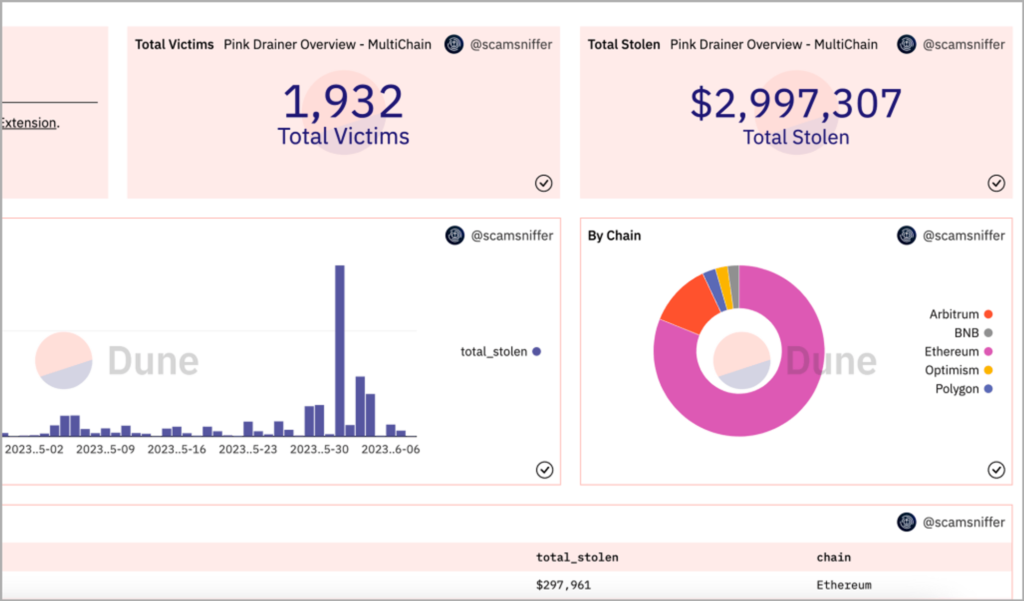
The latest notorious wallet drainer is Pink Drainer. According to Scam Sniffer, Taylor Monahan discovered Pink Drainer through her on-chain monitoring bot. Pink Drainer is known to have hacked over 7 Discord servers, affecting 2,484 victims. The total amount of crypto assets stolen has reached over $3 million, with affected on-chains including Polygon, Optimism, BNB, Arbitrum, and Ethereum.
Pink Drainer’s modus operandi involves social engineering and works by posing as journalists from prominent news outlets offering interviews. The interviewees are then asked to authenticate themselves with a Know Your Customer (KYC) process, where a phishing link is provided.
Another tactic is to ask Discord admins to initiate a fake Carl verification and add bookmarks containing malicious code. These codes are used to steal users’ authentication tokens. Once access is gained, Pink Drainer will remove other admins and continue the theft.
Conclusion
With the growing interest in crypto and the myriad of new innovations being offered, it’s inevitable that phishing and other malicious practices will continue to proliferate. That’s why it’s critical for crypto users to arm themselves with comprehensive information and rigorously protect their assets to fend off bad actors. In crypto, individuals are responsible for their own assets. If those assets are lost or stolen, recovery can be a challenge. Therefore, caution, extensive research, and knowledge of the crypto industry can save your valuable assets.
Read more: What is Crypto Scam and How Do You Avoid it?
References
- Chaimaka Atueyi, It’s The Crypto Drainers Rave! – This is How To Protect Your Wallets, Nigeriabitcoincommunity, accessed on 10 October 2023.
- Bill Toulas, Hackers steal $3 million by impersonating crypto news journalists, Bleepingcomputer, accessed on 10 October 2023.
- Fun, New Scam as a Service Provider: Venom Drainer, Scamsniffer, accessed on 10 October 2023.
- Immunebytes, Ice Phishing: What Is It, And How Does It Jeopardize Blockchain And Web3?, accessed on 10 October 2023.
- Forta Network, Breaking the Ice: a Phishing Deep Dive, Forta, accessed on 10 October 2023.
- Jesse Coghlan, Pink, Pussy, Venom, Inferno — Drainers coming for a crypto wallet near you, Cointelegraph, accessed on 10 October 2023.
- Anna Baydakova, This Is How Scammers Can Drain Your Crypto Wallet, Coindesk, accessed on 10 October 2023.
Share