Understanding Self-Custody: How to Store Your Crypto Safely

In the crypto community, there is a popular expression about storing crypto assets: “not your keys, not your crypto”. The point of this expression is that if you don’t have the key to your asset, then the asset is not truly yours. This is related to the decentralization principle, where you should have complete control over your assets. Storing crypto assets independently is also commonly referred to as self-custody. This article will fully discuss what is self-custody, how self-custody works, and the steps you need to take to keep your assets safe.
Article Summary
- 👤 Self-custody refers to storing crypto assets independently in a wallet without the need for a third party.
- 🔐 In a self-custody system, you will determine a password and get a private key or usually called a recovery or seed phrase. This private key is the only way you can get access to the assets inside.
- 🗂️ Crypto private wallets are divided into two, hardware wallets and software wallets. Both have advantages and disadvantages. Hardware wallets are the most secure because they don’t connect to the internet while digital wallets are free and easy to use.
- ⚠️ In a self-custody system, you are fully responsible for the security of your crypto assets. You need to understand a number of important things to ensure your assets are stored safely.
What is Self-Custody?
The FTX event in early November served as a reminder of the importance of how we store our crypto. This again raises the debate about keeping in exchange (custody wallet) or using self-custody. In a custodial wallet, exchanges like Pintu, Binance, and FTX are in charge of storing your crypto assets and keeping them safe. All crypto exchange exchanges do not have the right to use your crypto assets without consent. However, many people prefer to have full control over their crypto assets. This is the function of non-custodial wallets.
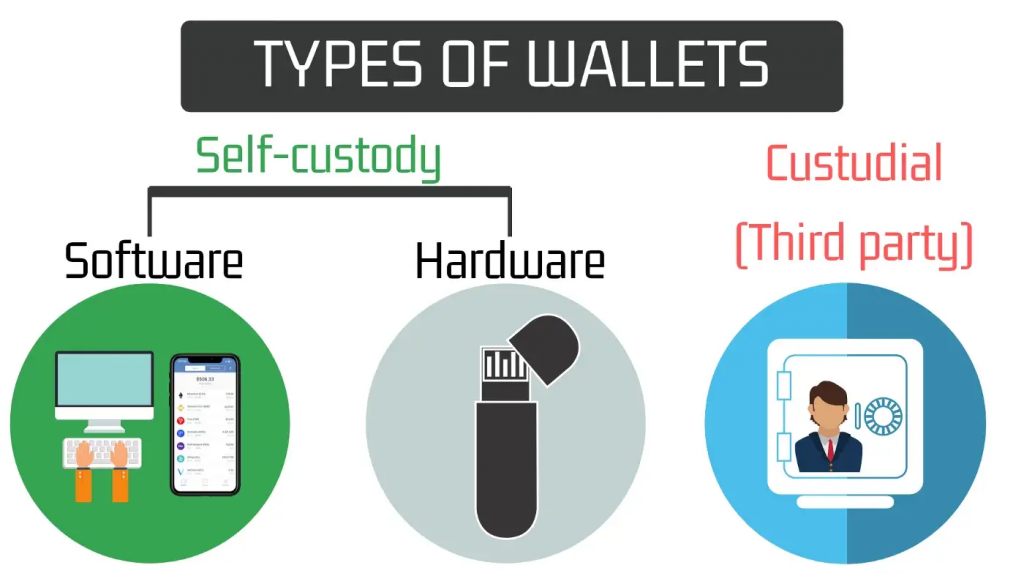
Non-custodial or self-custody is when you store crypto assets independently in a wallet without the need for a third party. It’s the same as keeping fiat money in your own wallet and not in the bank. The purpose and function of self-custody in crypto is to ensure that our crypto assets are under our full control. The concept of self-custody itself is in line with the principle of crypto decentralization where we no longer need authorities or third-party companies.
In crypto self-custody, you can choose from dozens of non-custodial wallets that are online or offline. Both types of wallets have their advantages and disadvantages which we will discuss later. However, both of them give you control over your crypto assets.
The FTX incident reminds us again of the "Not your keys, not your crypto"principle, and how we need to choose the right CEX to store crypto assets. In this case, Pintu has released "Pintu's transparency report"regarding the integrity of Pintu's user assets and how we ensure your assets are safe.
So, what makes the self-custody system safer and more preferable than the custodial system? To answer this question, we must understand how self-custody and non-custodial wallets work.
block-heading joli-heading" id="how-self-custody-works">How Self-Custody Works
In a self-custody system, you will set a password and get a private key or also called seed phrase. This private key is the most important component in a self-custody system because it is the only way you (or someone else) can access the assets inside. A seed phrase consists of 12, 18, or 24 random words in a specific order. When you want to access your wallet, you must enter the seed phrase in the correct word order or you will not be able to access it.
Did you know? A man named James Howell threw away his hard drive which turned out to be holding 7,500 BTC. Howell can't access his BTC because this hard drive stores the private key. This means that Howell can't access an insane amount of BTC. So, keep your private key, and don't become the next James Howell!
In addition to having a private key, a crypto wallet also has a public key, a public address for receiving and sending crypto assets, and interacting with decentralized applications (DApps). This is the address you can find when searching for transactions on sites like Etherscan and BscScan.
So, why is your wallet address called a public key? This is because it also acts like a key. You need to unlock this by agreeing to the “sign”command every time you interact with a new platform. It is also useful as a layer of security against spoofing.
Difference between Custody and Non-Custodial
The difference between custodial and non-custodial is where you keep your assets. In a custody wallet, you entrust your crypto assets to a centralized exchange (CEX) and they (supposedly) hold your assets until you sell or transfer them. Meanwhile, the non-custodial system stores assets in a private crypto wallet under your full responsibility.
In addition, using a custodial wallet on an exchange makes it easy for you to buy, sell, and send crypto because this is what a CEX does. Meanwhile, personal crypto wallets are usually a bit more complicated. In a non-custodial wallet, you need to understand gas fees, how to send and receive transactions, and how to interact with the different DEXs. However, in the end, this is done so that you have complete control of your personal assets.
Is Self-Custody Safe?
Self-custody technology has developed rapidly since its inception. Today, most of the security risks in using self-custody wallets come from the user side. Therefore, the security of private crypto wallets also depends on their users to store private keys safely and not interact with malicious sites.
Finally, in custodial storage on CEX, you don’t need to separate your wallet because wallets on exchanges can store all types of crypto assets. Meanwhile, not all self-custody wallets are compatible with multiple blockchains. Digital wallets such as MetaMask are specifically made for Ethereum-formatted tokens such as ERC20. On the other hand, a hardware wallet like Ledger Nano X can support multiple blockchains.
Both asset storage systems have advantages and disadvantages and you need to choose the one that suits you. The sections below will explain the types of self-custody wallets.
Types of Self Custody
Digital Wallet
A crypto digital wallet is a self-custody wallet that connects to the internet. Digital wallets are also commonly referred to as hot wallets (called hot because they are connected to the internet). In general, there are two types of digital wallets, wallets as mobile applications and browser extensions.
The main advantages of this type of self-custody crypto wallet are that it is lightweight, free, and can be used anywhere. The presence of a digital wallet is also one of the reasons why people use self-custody. Digital wallet only requires an internet connection and popular browsers such as Chrome, Microsoft Edge, and Safari.
However, the weakness of digital wallets is security issues. These digital wallets are highly susceptible to fraudulent scams such as phishing, fake giveaways, and spoofing. These scams try to take your private key or make you interact with the platform and drain all your assets.
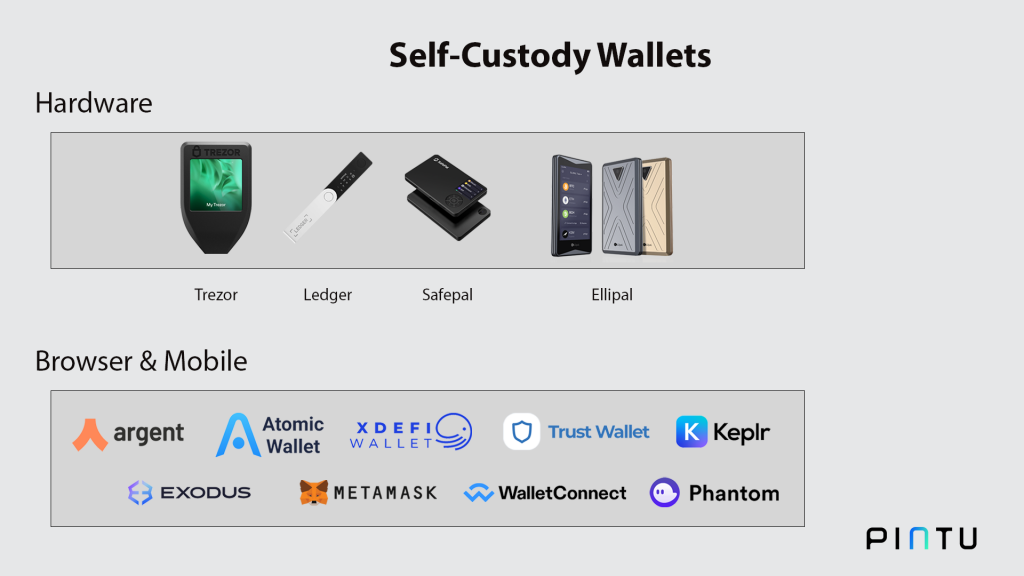
Examples of digital wallets: MetaMask, XDeFi, Trust Wallet, Wallet Connect, Atomic Wallet, Exodus Wallet, argent, Phantom wallet, and Keplr.
Physical Wallet
A hardware or physical crypto wallet is a special gadget that stores your crypto assets. This type of wallet is also commonly referred to as a cold wallet because it is not connected to the internet network. Hardware wallets have more sophisticated security and they can only be used after connecting using a USB. It is the most secure crypto storage tool. However, hardware wallets are not cheap (1-3 million rupiah) and you can still lose your assets if you lose this device.
Another type of physical crypto wallet is a metal board that prints 24 recovery seed sentences. Ledger sells this iron wallet at a price of 1.5 million where each side can store 12 words and you can change each word via shifting letters.
In addition, physical wallet technology is getting more and more sophisticated. Some hardware wallets give you the ability to buy and sell crypto right from the device. Most hardware wallets are also multichain where you can store various crypto assets from multiple blockchain networks.
Examples of some popular physical wallets are Trezor, Ledger, Ellipal, and Safepal.
Steps to Ensure Your Crypto Assets are Safe

1. Don’t Store Private Keys Online
One of the main principles of using a non-custodial digital wallet is not to store private keys online. This is especially important for digital crypto wallets like MetaMask. Try to save your private key manually on paper or in a place that only you have access to.
This is to prevent private keys from being lost due to hacking of devices and via the internet. Applications such as browsers and social media are easy entry points for hackers who want to take your private key.
2. Store Crypto Assets In Multiple Places
Another important thing you can do is divide where you store your crypto asset. You can spread your assets in some of the crypto wallets mentioned above. This is a basic security practice to prevent unexpected events. For example, 50% of your assets can be stored in a physical wallet, 25% in the MetaMask wallet that you normally use, and the remaining 25% in exchange. With this, you will not lose all your assets in the event of a hack or other unexpected incident.
The general rule of thumb is always to keep the majority of your assets in the safest place and spread the rest for short and medium-term trading needs.
3. Understand Crypto Scams
Lastly, you need to understand some of the common fraud methods in the crypto industry. Some of these fraud methods also specifically target crypto users who use digital non-custodial wallets. Examples of scams that target non-custodial wallets are Spoofing, fake airdrops, and phishing.
In 2021, the number of losses due to fraud reached $7.8 billion USD in 2021, an increase of 82% from 2020. According to Chainalysis, the highest number of crypto losses occurred in bull markets.
These three types of fraud have different methods with the same goal: to get you connected to fake sites that will drain your crypto assets. Usually, you will be instructed to interact with a smart contract, connect your digital wallet to a site, or follow a modified link.
Therefore, always pay attention to the address of the site you visit (whether it is official or not), don’t be tempted by the offers of free money, and always verify independently.
You can understand more about fraud in crypto in the article “What is Crypto Scam and How Do You Avoid it?“.
Buying Cryptocurrencies in Pintu
You can start investing in cryptocurrencies by buying them in the Pintu app. Here’s how to buy crypto on the Pintu application:
- Create a Pintu account and follow the process of verifying your identity to start trading.
- On the homepage, click the deposit button and top up the Pintu balance using your preferred payment method.
- Go to the market page and look for your favorite crypto assets.
- Click buy and fill in the amount you want.
- Now you have crypto as an asset!
In addition, the Pintu application is compatible with various popular digital wallets such as Metamask to facilitate your transactions. Go and download the Pintu cryptocurrency app on Play Store and App Store! Pintu is regulated and supervised by CoFTRA and Kominfo.
You can also learn more crypto through the various Door Academy articles which are updated every week! All Pintu Academy articles are for educational purposes, not financial advice.
References
- Ian Kane, Self-Custody Matters in Crypto, Dappradar, accessed on 21 November 2022.
- Lyle Daly, How to Store Cryptocurrency, The Motley Fool, accessed on 22 November 2022.
- Anthony Clarke, Are noncustodial crypto wallets a practical option for the everyday hodler?, Coin Telegraph, accessed on 22 November 2022.
- Jackson Wood, Custodial Wallets vs. Non-Custodial Crypto Wallets, Coin Desk, accessed on 23 November 2022.
- Andrew Asmakov, Non-Custodial vs Custodial Wallets: What’s the Difference?, Decrypt, accessed on 24 November 2022.
- Helen Partz, Simple steps to keep your crypto safe, Coin Telegraph, accessed on 25 November 2022.
Share


