Staying Secure in the Web3 Era: Best Practices You Need to Know
Have you ever received an email notifying you that you got a crypto airdrop, only to find your assets vanished after clicking the link and connecting your wallet? This is a classic example of a phishing attack in the Web3 world. Beyond phishing, numerous other scams can also pose financial risks to users. What scams should you be aware of, and how can you stay safe on Web3? Discover more in this article.
Article Summary
- ☠️ Scams are among the biggest crimes in the crypto world. Although the total losses decreased in 2023 compared to the previous year, the overall trend of scam activities shows a rise.
- 🚨 Scammers in the Web3 world often exploit users’ emotions of FOMO (Fear of Missing Out) and greed.
- ⚠️ Common scams in the Web3 world include romance (pig butchering), phishing, airdrop scams, smart contract exploitation, dusting attacks, and rug pulls.
- 🔰 Using an MPC wallet and following good security practices can significantly enhance protection against scams in the Web3 world.
Scams in the Web3 World
Web3 brings significant transformations through blockchain technology and decentralization. However, it also introduces substantial security challenges. As blockchain technology advances, so do the tactics of hackers (scammers) who continually develop new methods to exploit system vulnerabilities and defraud users.
According to Chainalysis data, scams are among the biggest crimes in the crypto world. Although total losses in 2023 decreased compared to the previous year, scam activities are on the rise.
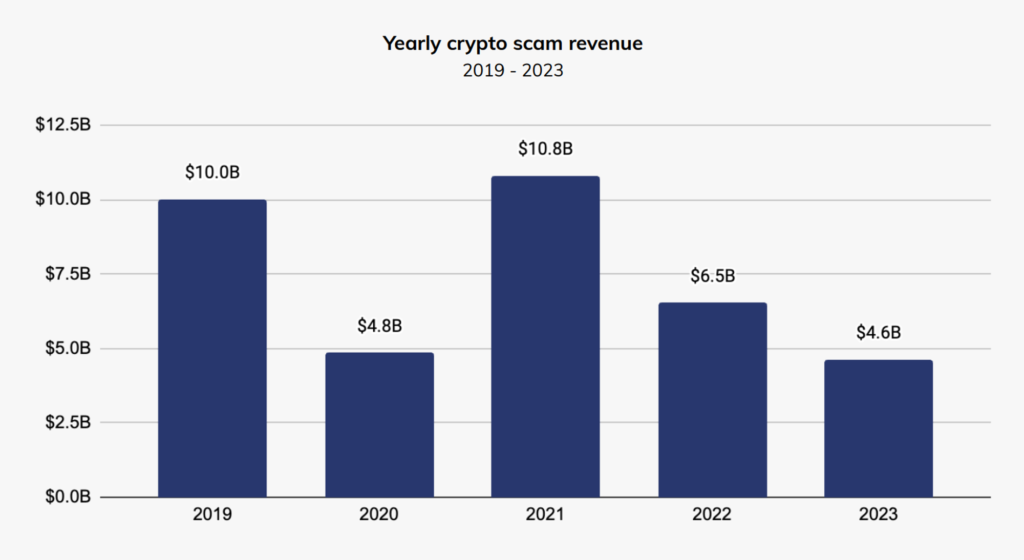
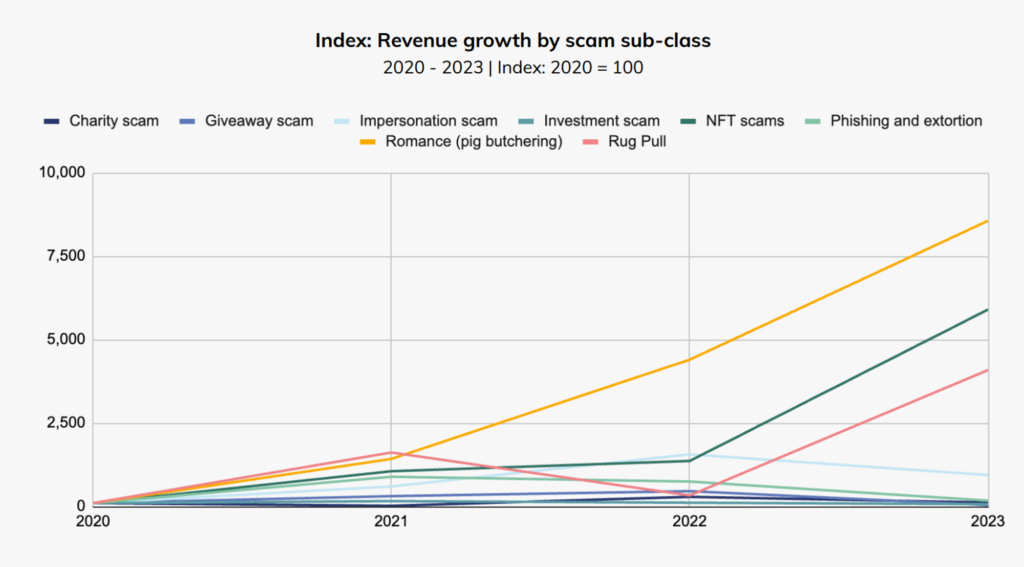
Chainalysis has categorized on-chain scams based on its methodology. It identifies certain patterns and criteria. All scam activities involve deceiving targets in various ways.
In 2023, romance scams (pig butchering), NFT scams, and rug pulls saw significant increases. The average payout for romance (pig butchering) and NFT scams were $4,593 and $3,095, respectively.
The term "pig butchering" describes the lengthy and manipulative process used by scammers to "fatten up" a victim before "butchering" them by stealing their assets.
Aleph Zero highlights that FOMO (Fear of Missing Out) and greed are two emotions commonly exploited by scammers in the online world, including the crypto and Web3 space.
Scammers use techniques such as limited-time investment offers, promises of huge returns, and psychological manipulation using false success stories. These tactics, among others, allow scammers to exploit individuals in the Web3 world for personal gain.
Types of Web3 Scams and How to Prevent Them
1. Romance (Pig Butchering)
Scammers create fake romantic relationships to lure victims into giving them money or sensitive information, often involving fake crypto investments.
Impact: Victims suffer significant financial losses and psychological trauma.
How to avoid:
- Verify the identity and background of the person before getting involved.
- Never send money or invest based on advice from someone you’ve just met.
2. Phishing
Scammers send emails, messages, or create fake websites that mimic popular crypto services to steal users’ credentials.
Impact: Users may unknowingly reveal their login information or private keys to scammers, who can then steal their crypto assets.
How to avoid:
- Never click on links in unknown emails or social media like Twitter.
- Verify website URLs to ensure you are accessing an authorized site.
- Enable two-factor authentication (2FA) on your account.
3. Unknown Tokens Listed in Wallet
The appearance of unknown tokens in your wallet, even if you didn’t purchase them, could be part of an airdrop phishing or a dusting attack.
Airdrop Phishing: Interacting with the token may redirect you to a phishing site that attempts to steal your login information or private key.
Another possibility is that when you try to send or exchange tokens, the transaction will fail, but the gas fee you paid will go to the scammer’s wallet.
Dusting Attack: These tokens may be used to track wallet activity and identify the wallet owner.
Impact: Users may lose funds in their wallets.
How to avoid:
- Do not try to send, exchange, or sell these tokens.
- Hide the tokens to avoid accidental interactions.
4. Airdrops and Giveaway Scams
Scammers promote fake airdrops or giveaways that promise free crypto rewards but require users to send a certain amount of crypto in advance as a “registration fee” or to “verify” their Web3 wallet.
Impact: Users lose the crypto they sent and receive no rewards.
How to avoid:
- Never send crypto as an “enrollment fee” or to “verify” a wallet.
- Verify the legitimacy of the airdrop or giveaway through official sources before participating.
- Avoid offers that promise very high returns.
5. Smart Contract Exploitation
Scammers exploit weaknesses in smart contract code to steal funds or manipulate contract functions.
Impact: Users lose funds locked in the exploited smart contract. Only the scammer can withdraw the funds.
How to avoid:
- Use legitimate platforms.
- Before interacting with smart contracts, check the code using blockchain explorers like Etherscan, Solscan, Arbiscan, etc.
6. Rug Pulls
Developers create a crypto or DeFi project with the intention to defraud. They raise funds from investors, then withdraw all funds (rug pull) and abandon the project.
Impact: Investors lose all the funds they invested in the project.
How to avoid:
- Verify that the development team is known and reputable.
- Research the project thoroughly, including third-party security audits.
- Pay attention to the crypto project’s community on social media. If a project lacks an active community, consider not investing in it.
MPC Wallet for Advanced Web3 Security
The Web3 platform leverages blockchain technology to give users full control over their data and digital assets. While Web3 offers numerous advantages, it is also vulnerable to fraud and increasingly sophisticated cyberattacks.
To address these challenges, the MPC (Multi-Party Computation) Wallet is a leading solution. An MPC Wallet divides a user’s private key into multiple parts and stores it at various trusted entities. It ensures that no single party has full access to the key. This technology enhances security and helps protect users from various types of fraud in the Web3 world.
Read more about What is an MPC Wallet?
Pintu Web3 Wallet is a Web3 wallet that utilizes MPC technology. This technology can significantly enhance the security of your crypto assets and reduce the risk of fraud, including wallet drainers.
Pintu Web3 Wallet also features a Fraud Detection system that can identify fraudulent activities in smart contracts. Before you interact with a smart contract, Pintu Web3 Wallet will provide a warning. It allows you to decide whether to proceed or cancel the transaction.
Use Cases of MPC Web3 Wallet in Preventing Fraud
- Reduces the risk of a single point of failure
By dividing the private key into multiple parts, the risk associated with a single point of failure is significantly reduced. Scammers cannot gain full access by stealing just one part of the key. This method enhances the Web3 security.
- Improves transaction security
Transactions must be approved by multiple parts of the distributed key. It adds an additional layer of security. Scammers would need to collect all parts of the key to authorize a malicious transaction, which is significantly more difficult.
- Integration with additional security protocols
An MPC Wallet can be integrated with additional security protocols such as two-factor authentication (2FA) and biometric verification, further enhancing overall security.
Conclusion
Scams in the Web3 world are common and costly to users. Using an MPC Wallet, such as the Pintu Web3 Wallet, is an effective solution to prevent this threat.
Although no solution is completely risk-free, combining technologies like MPC Wallets with strong security practices can significantly enhance protection against Web3 threats.
How to transact on dApps using Pintu Web3 Wallet
To make various transactions on dApps, including swaps, buying and selling, and staking tokens, you simply need to connect your Pintu Web3 Wallet with dApps via WalletConnect.
To connect your wallet with the dApp, follow these steps:
- Visit the dApp website on your laptop or mobile browser, for example, Pancakeswap.
- On the top right of the site, click ‘Connect Wallet’.
- Choose ‘WalletConnect,’ and a QR code will be displayed.
- Open the Web3 page on your Pintu account and scan the QR code using ‘WalletConnect’.
- As an alternative, you can use your smartphone to copy the dApp URL on the top right of the QR code and then paste it into the WalletConnect camera on the Pintu Web3 Wallet.
- Succes! Your Pintu Web3 Wallet is now connected to the dApp.
Once your wallet is connected to the dApp, you can transact on its available features.
References
- Chainanalysis, The 2024 Crypto Crime Report, Chainanalysis, accessed 4 June 2024.
- Aleksander Baczkowski, How to stay safe and secure in Web3? Key takeaways from Podcast Episode 1, Medium, accessed 4 June 2024.
- Builder DAO, Web3 Security: Uncovering the Hidden $100 Billion Market, Medium, accessed 4 June 2024.
Share


